Este es un "copiar y pegar" Cómo! La forma más sencilla de seguir este tutorial es utilizar un cliente de línea de comandos/cliente SSH (como PuTTY para Windows) y simplemente copiar y pegar los comandos (excepto cuando tenga que proporcionar información propia como direcciones IP, nombres de host, contraseñas,... ). Esto ayuda a evitar errores tipográficos.
ISP-ServerSetup -Ubuntu 5.10 "Breezy Badger"
Versión 1.0
Autor:Till Brehm , FalkoTimme
Esta es una descripción detallada de los pasos a seguir para configurar un Ubuntu servidor basado (Ubuntu 5.10 - Breezy Badger) que ofrece todos los servicios que necesitan los ISP y los hosters (servidor web (compatible con SSL), servidor de correo (con SMTP-AUTH y TLS), servidor DNS, servidor FTP, servidor MySQL, POP3/POP3s/ IMAP/IMAP, cuota, cortafuegos, etc.).
Usaré el siguiente software:
- Servidor web:Apache 2.0.x
- Servidor de correo:Postfix (más fácil de configurar que sendmail; tiene un historial más corto de agujeros de seguridad que sendmail)
- Servidor DNS:BIND9
- Servidor FTP:proftpd
- POP3/POP3s/IMAP/IMAPs:en este ejemplo, puede elegir entre el formato de buzón UNIX tradicional (luego usamos ipopd/ uw-imapd) o el formato Maildir (en este caso usaremos Courier-POP3/Courier-IMAP).
- Webalizer para estadísticas de sitios web
Al final, debe tener un sistema que funcione de manera confiable y esté listo para el panel de control de alojamiento web gratuito ISPConfig (es decir, ISPConfig se ejecuta en él fuera del caja).
Quiero decir primero que esta no es la única forma de configurar dicho sistema. Hay muchas maneras de lograr este objetivo, pero este es el camino que tomo. ¡No emito ninguna garantía de que esto funcione para usted!
Requisitos
Para instalar dicho sistema necesitará lo siguiente:
- Un CD de instalación de Ubuntu (disponible aquí:http://www.ubuntu.com/download/)
- Una conexión a Internet ya que describiré una instalación de red en este documento.
1 Sistema TheBase
Inserte su CD de instalación de Ubuntu en su sistema y arranque desde él (ingrese servidor en el indicador de inicio para instalar solo un sistema base adecuado para servidores).
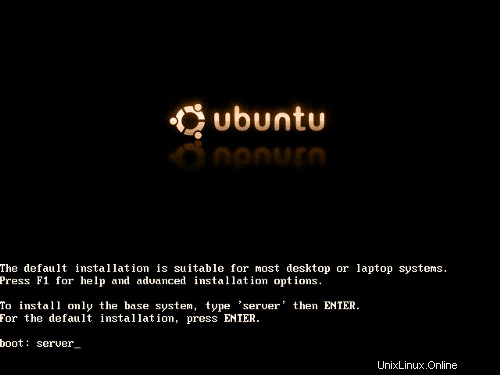
Comienza la instalación y primero tienes que elegir tu idioma:
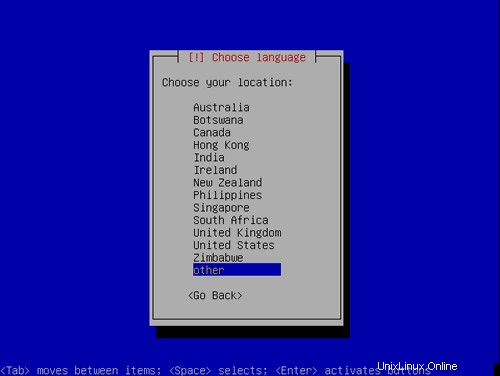
Elige tu ubicación:
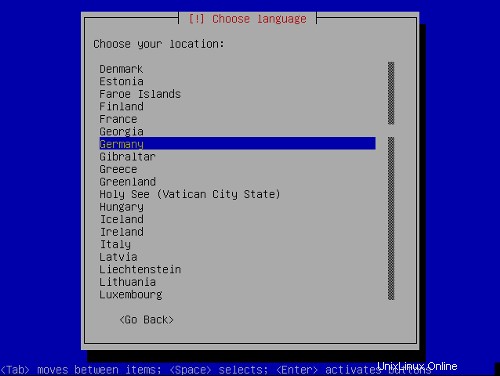
Elija un diseño de teclado:


La detección de hardware comienza:
Ingrese el nombre de host. En este ejemplo, mi sistema se llama servidor1 .ejemplo.com ,entonces ingreso servidor1 :
Ahora creamos las particiones. Seleccione Editar manualmente la tabla de particiones . Si ya hay algunas particiones, elimínelas primero seleccionándolas, presione regresar y luego seleccione eliminar.

Usaré el siguiente esquema de partición:
/arranque 50 MB
/intercambiar 1GB
/ 10 GB
/var el resto del disco duro
Crear una partición:Seleccione su disco duro (en mi caso SCSI1), presione enter, luego:

Crear una tabla de particiones:seleccione ESPACIO LIBRE , presiona enter, luego:

1) Seleccione Crear nueva partición .
2) Introduzca el tamaño de la partición. Los valores se pueden ingresar en MB y GB o en porcentaje (%)
3) Seleccione el tipo de partición:primary
4) Seleccione la ubicación de la partición:comienzo
5) Cambiar Usar como :Usaré EXT3 para todas las particiones excepto la partición de intercambio, que es de tipo intercambio.
6) Cambio:seleccione el punto de montaje
7) Seleccione He terminado de configurar la partición
Repita esto para todas las particiones en la tabla de particiones anterior.
Ahora su tabla de particiones debería verse similar a esto:
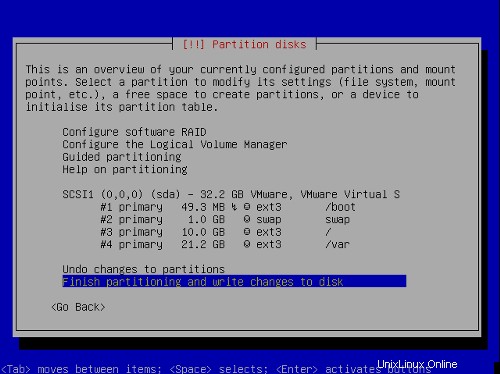
Seleccione Finalizar la partición y escribir los cambios en el disco , entonces Sí ,para continuar con el siguiente paso.
Ahora se está instalando el sistema base:
Configura tu zona horaria:

Configurar un usuario:

La primera etapa del proceso de instalación finaliza y el servidor arranca en Ubuntu Linux instalado.
2 Instalación y configuración del resto del sistema
Habilitar usuario raíz
Ahora puedo iniciar sesión con el nombre de usuario y la contraseña que ingresé anteriormente. Primero habilito el usuario root para facilitar la instalación. Puede desactivarlo más tarde si lo desea.
sudopasswd root
su
Ahora iniciamos sesión como usuario root.
Configurar la red
Debido a que el instalador de Ubuntu ha configurado nuestro sistema para obtener su configuración de red a través de DHCP, tenemos que cambiar eso ahora porque un servidor debe tener una dirección IP estática . Editar /etc/network/interfaces y ajústelo a sus necesidades (en este ejemplo de configuración usaré la dirección IP 192.168.0.100 ):
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
# The loopback network interface
auto lo
iface lo inet loopback
# This is a list of hotpluggable network interfaces.
# They will be activated automatically by the hotplug subsystem.
mapping hotplug
script grep
map eth0
# The primary network interface
auto eth0
iface eth0 inet static
address 192.168.0.100
netmask 255.255.255.0
network 192.168.0.0
broadcast 192.168.0.255
gateway 192.168.0.1 |
Si desea agregar la dirección IP 192.168.0.101 a la interfaz eth0 debe cambiar el archivo para que se vea así:
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
# The loopback network interface
auto lo
iface lo inet loopback
# This is a list of hotpluggable network interfaces.
# They will be activated automatically by the hotplug subsystem.
mapping hotplug
script grep
map eth0
# The primary network interface
auto eth0
iface eth0 inet static
address 192.168.0.100
netmask 255.255.255.0
network 192.168.0.0
broadcast 192.168.0.255
gateway 192.168.0.1
auto eth0:0
iface eth0:0 inet static
address 192.168.0.101
netmask 255.255.255.0
network 192.168.0.0
broadcast 192.168.0.255
gateway 192.168.0.1 |
Luego reinicie su red:
/etc/init.d/networkingrestart
Editar /etc/hosts y agregue sus nuevas direcciones IP:
127.0.0.1 localhost.localdomain localhost server1
192.168.0.100 server1.example.com server1
192.168.0.101 virtual-ip1.example.com virtual-ip1
# The following lines are desirable for IPv6 capable hosts
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
ff02::3 ip6-allhosts |
Configuración del nombre de host
echo server1.example.com> /etc/hostname
/bin/nombre de host -F /etc/nombre de host
Edite /etc/apt/sources.listY actualice su instalación de Linux
Editar /etc/apt/sources.list .Debería verse así:
# deb cdrom:[Ubuntu 5.10 _Breezy Badger_ - Release i386 (20051012)]/ breezy main restricted
deb http://de.archive.ubuntu.com/ubuntu breezy main restricted
deb-src http://de.archive.ubuntu.com/ubuntu breezy main restricted
## Major bug fix updates produced after the final release of the
## distribution.
deb http://de.archive.ubuntu.com/ubuntu breezy-updates main restricted
deb-src http://de.archive.ubuntu.com/ubuntu breezy-updates main restricted
## Uncomment the following two lines to add software from the 'universe'
## repository.
## N.B. software from this repository is ENTIRELY UNSUPPORTED by the Ubuntu
## team, and may not be under a free licence. Please satisfy yourself as to
## your rights to use the software. Also, please note that software in
## universe WILL NOT receive any review or updates from the Ubuntu security
## team.
deb http://de.archive.ubuntu.com/ubuntu breezy universe
deb-src http://de.archive.ubuntu.com/ubuntu breezy universe
## Uncomment the following two lines to add software from the 'backports'
## repository.
## N.B. software from this repository may not have been tested as
## extensively as that contained in the main release, although it includes
## newer versions of some applications which may provide useful features.
## Also, please note that software in backports WILL NOT receive any review
## or updates from the Ubuntu security team.
# deb http://de.archive.ubuntu.com/ubuntu breezy-backports main restricted universe multiverse
# deb-src http://de.archive.ubuntu.com/ubuntu breezy-backports main restricted universe multiverse
deb http://security.ubuntu.com/ubuntu breezy-security main restricted
deb-src http://security.ubuntu.com/ubuntu breezy-security main restricted
deb http://security.ubuntu.com/ubuntu breezy-security universe
deb-src http://security.ubuntu.com/ubuntu breezy-security universe |
apt-get update
apt-get upgrade
Instalar SSH Daemon
apt-get install sshopenssh-server
Instalar/eliminar algún software
Ahora instalemos algún software que necesitemos más adelante y eliminemos algunos paquetes que no necesitamos:
apt-get install binutilscpp cpp-4.0 fetchmail flex gcc gcc-4.0 libarchive-zip-perl libc6-dev libcompress-zlib-perllibdb4.3 -dev libpcre3 libpopt-dev linux-kernel-headers lynx m4 make ncftp nmapopenssl perl perl-modules unzip zip zlib1g-dev autoconf automake1.9 libtoolbison autotools-dev cpp g++ (en 1 línea!!)
Cuota
apt-obtener cuota de instalación
Editar /etc/fstab para verse así (agregué ,usrquota,grpquota a las particiones con el punto de montaje / y /var ):
# /etc/fstab: static file system information.
#
#
proc /proc proc defaults 0 0
/dev/sda3 / ext3 defaults,errors=remount-ro,usrquota,grpquota 0 1
/dev/sda1 /boot ext3 defaults 0 2
/dev/sda4 /var ext3 defaults,usrquota,grpquota 0 2
/dev/sda2 none swap sw 0 0
/dev/hdc /media/cdrom0 udf,iso9660 ro,user,noauto 0 0
/dev/fd0 /media/floppy0 auto rw,user,noauto 0 0
|
Luego ejecuta:
touch /quota.user /quota.group
chmod 600 /quota.*
mount -o remount /
touch /var/quota.user /var/quota.group
chmod 600 /var/quota.*
mount -o volver a montar /var
quotacheck -avugm
quotaon -avug
Servidor DNS
apt-getinstall bind9
Por razones de seguridad, queremos ejecutar BIND en chroot, por lo que debemos realizar los siguientes pasos:
/etc/init.d/bind9 parada
Edite el archivo /etc/default/bind9 para que el demonio se ejecute como el usuario sin privilegios 'bind ', enrutado a /var/lib/named .Modifique la línea:OPTS=" -ubind " para que lea OPTIONS="-u bind-t /var/lib/named" :
OPTIONS="-u bind -t /var/lib/named" |
Cree los directorios necesarios en /var/lib :
mkdir -p /var/lib/named/etc
mkdir /var/lib/named/dev
mkdir -p /var/lib/named/var/cache/bind
mkdir -p /var/lib/named/var/run/bind/run
Luego mueva el directorio de configuración de /etc a /var/lib/named/etc :
mv /etc/bind /var/lib/named/etc
Cree un enlace simbólico al nuevo directorio de configuración desde la ubicación anterior (para evitar problemas cuando se actualice bindis en el futuro):
ln -s /var/lib/named/etc/bind/etc/bind
Hacer dispositivos nulos y aleatorios, y arreglar los permisos de los directorios:
mknod /var/lib/named/dev/nullc 1 3
mknod /var/lib/named/dev /random c 1 8
chmod 666 /var/lib/named/dev/null /var/lib/named/dev/random
chown -R bind:bind /var/lib/named/var/ *
chown -R enlazar:enlazar /var/lib/named/etc/bind
Necesitamos modificar el script de inicio /etc/init.d/ registro del sistema de sysklogd para que aún podamos obtener mensajes importantes registrados en los registros del sistema. Modifique la línea: SYSLOGD="-u syslog" para que diga:SYSLOGD="-u syslog -a /var/lib/named/dev/log" :
#! /bin/sh
# /etc/init.d/sysklogd: start the system log daemon.
PATH=/bin:/usr/bin:/sbin:/usr/sbin
pidfile=/var/run/syslogd.pid
binpath=/sbin/syslogd
test -x $binpath || exit 0
. /lib/lsb/init-functions
# Options for start/restart the daemons
# For remote UDP logging use SYSLOGD="-r"
#
SYSLOGD="-u syslog -a /var/lib/named/dev/log"
create_xconsole()
{
if [ ! -e /dev/xconsole ]; then
mknod -m 640 /dev/xconsole p
else
chmod 0640 /dev/xconsole
fi
chown root:adm /dev/xconsole
}
running()
{
# No pidfile, probably no daemon present
#
if [ ! -f $pidfile ]
then
return 1
fi
pid=`cat $pidfile`
# No pid, probably no daemon present
#
if [ -z "$pid" ]
then
return 1
fi
if [ ! -d /proc/$pid ]
then
return 1
fi
cmd=`cat /proc/$pid/cmdline | tr "\000" "\n"|head -n 1`
# No syslogd?
#
if [ "$cmd" != "$binpath" ]
then
return 1
fi
return 0
}
case "$1" in
start)
log_begin_msg "Starting system log daemon..."
create_xconsole
start-stop-daemon --start --quiet --exec $binpath -- $SYSLOGD
log_end_msg $?
;;
stop)
log_begin_msg "Stopping system log daemon..."
start-stop-daemon --stop --quiet --oknodo --exec $binpath --pidfile $pidfile
log_end_msg $?
;;
restart|force-reload|reload-or-restart|reload)
log_begin_msg "Restarting system log daemon..."
start-stop-daemon --stop --quiet --exec $binpath --pidfile $pidfile
sleep 1
start-stop-daemon --start --quiet --exec $binpath -- $SYSLOGD
log_end_msg $?
;;
*)
log_success_msg "Usage: /etc/init.d/sysklogd {start|stop|reload|restart|force-reload|reload-or-restart}"
exit 1
esac
exit 0 |
Reiniciar el loggingdaemon:
/etc/init.d/sysklogd restart
Inicie BIND y verifique /var/log/syslog por cualquier error:
/etc/init.d/bind9 start
MySQL
apt-getinstall mysql-server mysql-client libmysqlclient12-dev
mysqladmin -u root passwordyourrootsqlpassword
mysqladmin -h server1.example.com -u root password yourrootsqlpassword
Cuando ejecuta netstat-tap ahora debería ver una línea como esta:
tcp 0 0 localhost.localdo:mysql *:* LISTEN 2449/mysqld |
lo que significa que se puede acceder a MySQL en el puerto 3306. Puede ir a la siguiente sección (Postfix). Si no ve esta línea, edite /etc/mysql/my.cnf y comenta skip-networking :
# skip-networking |
Si tuviera que editar /etc/mysql/my.cnf tienes que reiniciar MySQL:
/etc/init.d/mysql restart
Postfix
Para instalar Postfix con SMTP-AUTH y TLS siga los siguientes pasos:
apt-get install postfixpostfix-tls libsasl2 sasl2-bin libsasl2-modules libdb3-util procmail (¡1 línea!)
dpkg-reconfigurepostfix
<- Sitio de Internet
<- NINGUNO
<- server1.example.com
<- servidor1.ejemplo.com, localhost.ejemplo.com, localhost
<- No
<- 127.0.0.0/8
<- 0
<- +
postconf -e 'smtpd_sasl_local_domain='
postconf -e 'smtpd_sasl_auth_enable =yes'
postconf -e 'smtpd_sasl_security_options =noanonymous'
postconf -e 'broken_sasl_auth_clients =yes'
postconf -e 'smtpd_recipient_restrictions =permit_sasl_authenticated,permit_mynetworks,reject_unauth_destination'
postconf -e 'inet_interfaces =all'
echo 'pwcheck_method:saslauthd'>> /etc/postfix/sasl/smtpd.conf
echo 'mech_list:inicio de sesión simple'>> /etc/postfix/sasl/smtpd.conf
mkdir /etc/postfix/ssl
cd /etc/postfix/ssl/
openssl genrsa - des3 -rand /etc/hosts -out smtpd.key 1024
chmod 600 smtpd.key
openssl req -new -key smtpd.key -out smtpd.csr
openssl x509 -req -days 3650 -in smtpd.csr -signkey smtpd.key -out smtpd.crt
openssl rsa -in smtpd.key -out smtpd.key.unencrypted
mv -f smtpd.key.unencrypted smtpd.key
openssl req -nuevo -x509 -extensiones v3_ca -keyout cakey.pem -out cacert.pem -days3650
postconf -e 'smtpd_tls_auth_only=no'
postconf -e 'smtp_use_tls =yes'
postconf - e 'smtpd_use_tls =yes'
postconf -e 'smtp_tls_note_starttls_offer =yes'
postconf -e 'smtpd_tls_key_file =/etc/postfix/ssl/smtpd.key'
postconf -e 'smtpd_tls_cert_file =/ etc/postfix/ssl/smtpd.crt'
postconf -e 'smtpd_tls_CAfile =/etc/postfix/ssl/cacert.pem'
postconf -e 'smtpd_tls_loglevel =1'
postconf -e 'smtpd_tls_received_header =yes'
postconf -e 'smtpd_tls_session_cache_timeout =3600s'
postconf -e 'tls_random_source =dev:/dev/urandom'
postconf -e 'myhostname =server1.example.com'
El archivo /etc/postfix/main.cf ahora debería verse así:
# See /usr/share/postfix/main.cf.dist for a commented, more complete version
smtpd_banner = $myhostname ESMTP $mail_name (Ubuntu)
biff = no
# appending .domain is the MUA's job.
append_dot_mydomain = no
# Uncomment the next line to generate "delayed mail" warnings
#delay_warning_time = 4h
myhostname = server1.example.com
alias_maps = hash:/etc/aliases
alias_database = hash:/etc/aliases
myorigin = /etc/mailname
mydestination = server1.example.com, localhost.example.com, localhost
relayhost =
mynetworks = 127.0.0.0/8
mailbox_size_limit = 0
recipient_delimiter = +
inet_interfaces = all
mailbox_command =
smtpd_sasl_local_domain =
smtpd_sasl_auth_enable = yes
smtpd_sasl_security_options = noanonymous
broken_sasl_auth_clients = yes
smtpd_recipient_restrictions = permit_sasl_authenticated,permit_mynetworks,reject_unauth_destination
smtpd_tls_auth_only = no
smtp_use_tls = yes
smtpd_use_tls = yes
smtp_tls_note_starttls_offer = yes
smtpd_tls_key_file = /etc/postfix/ssl/smtpd.key
smtpd_tls_cert_file = /etc/postfix/ssl/smtpd.crt
smtpd_tls_CAfile = /etc/postfix/ssl/cacert.pem
smtpd_tls_loglevel = 1
smtpd_tls_received_header = yes
smtpd_tls_session_cache_timeout = 3600s
tls_random_source = dev:/dev/urandom |
/etc/init.d/postfixrestart
La autenticación será realizada por saslauthd .Tenemos que cambiar algunas cosas para que funcione correctamente. Porque Postfix se ejecuta en /var/spool/postfix tenemos que hacer lo siguiente:
mkdir -p /var/spool/postfix/var/run/saslauthd
rm -fr /var/run/saslauthd
Ahora tenemos que editar /etc/default/saslauthd para activar saslauthd .Remove # in front of START=yes and add the line PARAMS="-m/var/spool/postfix/var/run/saslauthd" :
# This needs to be uncommented before saslauthd will be run automatically
START=yes
PARAMS="-m /var/spool/postfix/var/run/saslauthd"
# You must specify the authentication mechanisms you wish to use.
# This defaults to "pam" for PAM support, but may also include
# "shadow" or "sasldb", like this:
# MECHANISMS="pam shadow"
MECHANISMS="pam" |
Finally we haveto edit /etc/init.d/saslauthd .Change the line
dir=`dpkg-statoverride --list $PWDIR` |
to
#dir=`dpkg-statoverride --list $PWDIR` |
Then change thevariables PWDIR and PIDFILE and add the variable dir at the beginning of the file:
PWDIR="/var/spool/postfix/var/run/${NAME}"
PIDFILE="${PWDIR}/saslauthd.pid"
dir="root sasl 755 ${PWDIR}" |
/etc/init.d/saslauthd should now looklike this:
#!/bin/sh -e
NAME=saslauthd
DAEMON="/usr/sbin/${NAME}"
DESC="SASL Authentication Daemon"
DEFAULTS=/etc/default/saslauthd
PWDIR="/var/spool/postfix/var/run/${NAME}"
PIDFILE="${PWDIR}/saslauthd.pid"
dir="root sasl 755 ${PWDIR}"
createdir() {
# $1 = user
# $2 = group
# $3 = permissions (octal)
# $4 = path to directory
[ -d "$4" ] || mkdir -p "$4"
chown -c -h "$1:$2" "$4"
chmod -c "$3" "$4"
}
test -f "${DAEMON}" || exit 0
# Source defaults file; edit that file to configure this script.
if [ -e "${DEFAULTS}" ]; then
. "${DEFAULTS}"
fi
# If we're not to start the daemon, simply exit
if [ "${START}" != "yes" ]; then
exit 0
fi
# If we have no mechanisms defined
if [ "x${MECHANISMS}" = "x" ]; then
echo "You need to configure ${DEFAULTS} with mechanisms to be used"
exit 0
fi
# Add our mechanimsms with the necessary flag
PARAMS="${PARAMS} -a ${MECHANISMS}"
START="--start --quiet --pidfile ${PIDFILE} --startas ${DAEMON} --name ${NAME} -- ${PARAMS}"
# Consider our options
case "${1}" in
start)
echo -n "Starting ${DESC}: "
#dir=`dpkg-statoverride --list $PWDIR`
test -z "$dir" || createdir $dir
if start-stop-daemon ${START} >/dev/null 2>&1 ; then
echo "${NAME}."
else
if start-stop-daemon --test ${START} >/dev/null 2>&1; then
echo "(failed)."
exit 1
else
echo "${DAEMON} already running."
exit 0
fi
fi
;;
stop)
echo -n "Stopping ${DESC}: "
if start-stop-daemon --stop --quiet --pidfile "${PIDFILE}" \
--startas ${DAEMON} --retry 10 --name ${NAME} \
>/dev/null 2>&1 ; then
echo "${NAME}."
else
if start-stop-daemon --test ${START} >/dev/null 2>&1; then
echo "(not running)."
exit 0
else
echo "(failed)."
exit 1
fi
fi
;;
restart|force-reload)
$0 stop
exec $0 start
;;
*)
echo "Usage: /etc/init.d/${NAME} {start|stop|restart|force-reload}" >&2
exit 1
;;
esac
exit 0 |
Now start saslauthd :
/etc/init.d/saslauthd start
To see if SMTP-AUTHand TLS work properly now run the following command:
telnetlocalhost 25
After you haveestablished the connection to your postfix mail server type
ehlolocalhost
If you see thelines
250-STARTTLS
and
250-AUTH
everything is fine.

Type
quit
to return to thesystem's shell.
Courier-IMAP/Courier-POP3
Install Courier-IMAP/Courier-IMAP-SSL(for IMAPs on port 993) and Courier-POP3/Courier-POP3-SSL (for POP3s on port995).
apt-get install courier-authdaemoncourier-base courier-imap courier-imap-ssl courier-pop courier-pop-ssl courier-sslgamin libgamin0 libglib2.0-0 (oneline!)
<- No
<- OK
Then configurePostfix to deliver emails to a user's Maildir:
postconf -e 'home_mailbox=Maildir/'
postconf -e 'mailbox_command ='
/etc/init.d/postfix restart
Please go sureto enable Maildir underManagement -> Settings -> EMail in the ISPConfig web interface.
Apache
Run
apt-get install apache2apache2-common apache2-doc apache2-mpm-prefork apache2-utils libapr0 libexpat1ssl-cert (1line!)
apt-get install autoconf automake1.4 autotools-dev libapache2-mod-php4 libkrb53php4 php4-common php4-dev php4-imagick php4-mcrypt php4-rrdtool php4-sqlitephp4-curl php4-domxml php4-gd php4-imap php4-ldap php4-mcal php4-mhash php4-mysqlphp4-odbc php4-pear php4-xslt (1 line!)
<- Yes
Edit /etc/apache2/apache2.conf . Change
DirectoryIndex index.html index.cgi index.pl index.php index.xhtml |
to
DirectoryIndex index.html index.htm index.shtml index.cgi index.php index.php3 index.pl index.xhtml |
Edit /etc/mime.types and comment out the following lines:
#application/x-httpd-php phtml pht php
#application/x-httpd-php-source phps
#application/x-httpd-php3 php3
#application/x-httpd-php3-preprocessed php3p
#application/x-httpd-php4 php4 |
Edit /etc/apache2/mods-enabled/php4.conf and comment out the following lines:
<IfModule mod_php4.c>
# AddType application/x-httpd-php .php .phtml .php3
# AddType application/x-httpd-php-source .phps
</IfModule> |
Edit /etc/apache2/ports.conf and add Listen 443 :
Listen 80
Listen 443 |
Now we have toenable some Apache modules (SSL , rewrite and suexec ):
a2enmod ssl
a2enmod rewrite
a2enmod suexec
a2enmod include
Reload Apacheconfiguration:
/etc/init.d/apache2force-reload
Proftpd
apt-getinstall proftpd proftpd-common ucf
<- standalone
For security reasonsyou can add the following lines to /etc/proftpd.conf (thanks to Reinaldo Carvalho; more information can be found here:http://proftpd.linux.co.uk/localsite/Userguide/linked/userguide.html):
DefaultRoot ~
IdentLookups off
ServerIdent on "FTP Server ready."
and restart Proftpd:
/etc/init.d/proftpd restart
Webalizer
apt-getinstall webalizer
Install somePerl Modules needed by SpamAssassin (comes with ISPConfig)
apt-get installlibhtml-parser-perl libdb-file-lock-perl libnet-dns-perl
On To TheNext Step...
The configurationof the server is now finished, and we go on by installing ISPConfigon it.
3 Installing ISPConfig
I will installthe current ISPConfig version. Download the current ISPConfig version from http://www.ispconfig.org/downloads.htmto your /tmp directory.
Unpack the ISPConfig-archiveand change to the directory install_ispconfig :
tarxvfz ISPConfig*.tar.gz
cd install_ispconfig
Start the setupscript
./setup
The installer willnow compile an Apache with PHP5 that will run on port 81 and is needed by theISPConfig system itself. It will not interfere with your existing Apache installationso you can go on unworried.
When the ISPConfigApache is built, a custom SSL certificate is built. Therefore you are askeda few questions. You can accept the default values, or you can enter new valuesthere, this does not matter:
In step 7 (EncryptingRSA private key of CA with a pass phrase for security [ca.key] ) andstep 8 (Encrypting RSA private keyof SERVER with a pass phrase for security [server.key] ) of the certificatecreation process you are asked if you want to encrypt the respective key now.Choose n there becauseotherwise you will always be asked for a password whenever you want to restartthe ISPConfig system which means it cannot be restarted without human interaction!
If the compilationfails, the setup is stopped and all compiled files are removed. From the errormessage you get you should be able to see the reason for the failure (in mostcases a package (like the MySQL header files) is missing). Try to solve theproblem and the re-run ./setup .
In case of successthe setup goes on:
Pleasechoose your language. This is the language of the ISPConfig interface.
Afterwards youare shown the ISPConfig licence (BSD licence). Please read it carefully! Youaccept it by typing y .If you do not want to accept the ISPConfig licence, type n ,and the installation routine stops.
As installation mode I chose expert becausei want to set the website root to /var/www .When you are asked for installation mode, type 2 and hit return.
Now you are askif the daemons like postfix etc. are recognized correctly and for their filelocations, chose yes y .
When you are asked:
Web-Root:/home/www
Is this correct? [y/n]
choose n and enter /var/www as Web-Root.
Now you are askedfor some installation settings:
Pleaseenter your MySQL server: localhost
Please enter your MySQL user: root
Please enter your MySQL password: (Enter the password you chose when setting up the MySQL Server)
Please enter a name for the ISPConfigdatabase (e.g. db_ispconfig): db_ispconfig
Please enter the IP addressof the ISPConfig web (e.g. 192.168.0.1): 192.168.0.100 (Enteryour IP here)
Now you are askto enter the host and domain of your server. If your server has a host and domainname,enter them now. As this is a test install in my local network, I leave the hostempty and enter my IP address instead of the domain.
Pleaseenter the host name (e.g. www):
Please enter the domain (e.g.xyz.de): 192.169.0.100
Pleaseselect the protocol (http or https (SSL encryption)) to use to access the ISPConfigsystem:
1) HTTPS
2) HTTP
Your Choice: 1
After you haveanswered the questions ISPConfig should be duly installed. If you indicated www as host and xyz.com as the domain during the installation, you will find the ISPConfig interfaceunder https://www.xyz.de:81 or http://www.xyz.de:81 .Here you can login first with the user name admin and password admin . Itis recommended to change the password immediately! This can be done in the ISPConfigweb interface under Tools -> Changepassword .
Then go to Management-> Server -> Settings in the ISPConfig control panel and tickthe Maildir checkbox onthe EMail tab.
If your serverhas more than one IP address, please check if your additional IP addresses havebeen correctly detected by the installation routine under Management-> Server ->
Settings on the tab Server-> IP List .
You can find thewhole ISPConfig installation instructions here:http://www.ispconfig.org/manual_installation.htm
The ISPConfig manualscan be found here:http://www.ispconfig.org/documentation.htm
Links
- http://www.ubuntu.com
- http://www.ispconfig.org





















