Let's Encrypt es una autoridad de certificación ampliamente conocida que ofrece certificados SSL gratuitos para sitios web, lanzada en abril de 2016.
Con la ayuda del cliente Certbot, la creación, validación, firma, implementación y renovación de certificados están completamente automatizadas.
Requisitos
Siga los enlaces para tener la pila LAMP o solo el servidor web Apache instalado en su sistema.
LEER :Cómo instalar LAMP Stack en CentOS 8 / RHEL 8
LEER :Cómo instalar LAMP Stack en CentOS 7 / RHEL 7
Instalar cliente Certbot
Para generar e instalar un certificado para cualquier dominio, debe tener acceso a la terminal y el cliente Certbot ACME instalado en el sistema. El cliente Certbot automatiza la emisión e instalación de certificados sin tiempo de inactividad.
El cliente Certbot está disponible en el repositorio de EPEL para CentOS 7/RHEL 7. Pero debemos descargar el cliente Certbot manualmente para CentOS 8/RHEL 8 desde su sitio oficial.
### CentOS 8 / RHEL 8 ### yum install -y httpd mod_ssl curl -O https://dl.eff.org/certbot-auto mv certbot-auto /usr/local/bin/certbot-auto chmod 0755 /usr/local/bin/certbot-auto ### CentOS 7 ### rpm -ivh https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm yum install -y certbot python2-certbot-apache ### RHEL 7 ### rpm -ivh https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm subscription-manager repos --enable rhel-7-server-optional-rpms yum install -y certbot python2-certbot-apache
Crear servidor virtual
Crearemos un host virtual para el dominio:www.itzgeek.net.
Este host virtual maneja la versión HTTP de su dominio.vi /etc/httpd/conf.d/www.itzgeek.net.conf
Utilice la siguiente información.
<VirtualHost *:80>
ServerName itzgeek.net
ServerAlias www.itzgeek.net
DocumentRoot /var/www/www.itzgeek.net
<Directory /var/www/www.itzgeek.net>
Options -Indexes +FollowSymLinks
AllowOverride All
</Directory>
ErrorLog /var/log/httpd/www.itzgeek.net-error.log
CustomLog /var/log/httpd/www.itzgeek.net-access.log combined
</VirtualHost> Cree una raíz de documento para colocar sus archivos HTML.
mkdir -p /var/www/www.itzgeek.net
Coloque el archivo HTML dentro de la raíz del documento de su dominio.
echo "This is a test site @ www.itzgeek.net" > /var/www/www.itzgeek.net/index.html
Cambia el permiso del directorio.
chown -R apache:apache /var/www/www.itzgeek.net
Reinicie el servicio de Apache.
systemctl restart httpd
Crear/Actualizar Registro DNS
Vaya a su registrador de dominio y cree un registro A/CNAME para su dominio. Ej:www.itzgeek.net.
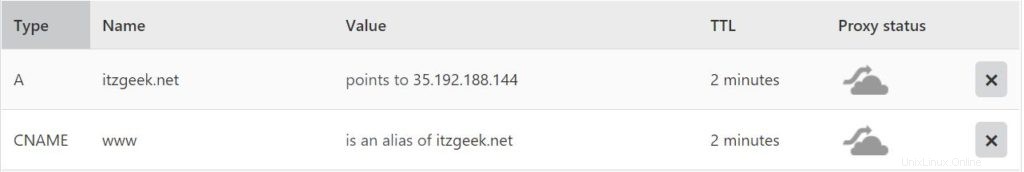
Espere un tiempo para permitir que el registro se propague.
Compruebe la propagación de DNS con la utilidad Nslookup yum install -y bind-utils.

Instalar el certificado SSL de Let's Encrypt
Use el comando certbot para generar e instalar el certificado Let's Encrypt.
### RHEL 8 ### /usr/local/bin/certbot-auto --apache ### CentOS 7 / RHEL 7 ### certbot --apache
Siga las indicaciones interactivas e instale el certificado.
Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator apache, Installer apache Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): itzgeek.web@gmail.com << Enter Email address to receive notifications - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must agree in order to register with the ACME server at https://acme-v02.api.letsencrypt.org/directory - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (A)gree/(C)ancel: A << Agree to Terms of Sevice - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: Y << Subscribe to Newsletter Which names would you like to activate HTTPS for? - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - 1: itzgeek.net 2: www.itzgeek.net - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Select the appropriate numbers separated by commas and/or spaces, or leave input blank to select all options shown (Enter 'c' to cancel): 2 << Choose the domain to install Let's Encrypt SSL certificate Obtaining a new certificate Performing the following challenges: http-01 challenge for www.itzgeek.net Waiting for verification... Cleaning up challenges Created an SSL vhost at /etc/httpd/conf.d/www.itzgeek.net-le-ssl.conf Deploying Certificate to VirtualHost /etc/httpd/conf.d/www.itzgeek.net-le-ssl.conf Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - 1: No redirect - Make no further changes to the webserver configuration. 2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for new sites, or if you're confident your site works on HTTPS. You can undo this change by editing your web server's configuration. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2 << Redirect from HTTP to HTTPS Redirecting vhost in /etc/httpd/conf.d/www.itzgeek.net.conf to ssl vhost in /etc/httpd/conf.d/www.itzgeek.net-le-ssl.conf - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Congratulations! You have successfully enabled https://www.itzgeek.net You should test your configuration at: https://www.ssllabs.com/ssltest/analyze.html?d=www.itzgeek.net - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/www.itzgeek.net/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/www.itzgeek.net/privkey.pem Your cert will expire on 2019-11-10. To obtain a new or tweaked version of this certificate in the future, simply run certbot-auto again with the "certonly" option. To non-interactively renew *all* of your certificates, run "certbot-auto renew" - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal. - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le
Cortafuegos
Configure el cortafuegos para permitir solicitudes HTTPS.
firewall-cmd --permanent --add-port=443/tcp firewall-cmd --reload
Verificar el certificado Let's Encrypt
Verifique el certificado de Let's Encrypt visitando la versión HTTPS de su sitio web.
http://tu-http-sitio-webO
https://tu-https-sitio-webAhora debería obtener una versión HTTPS de su sitio.
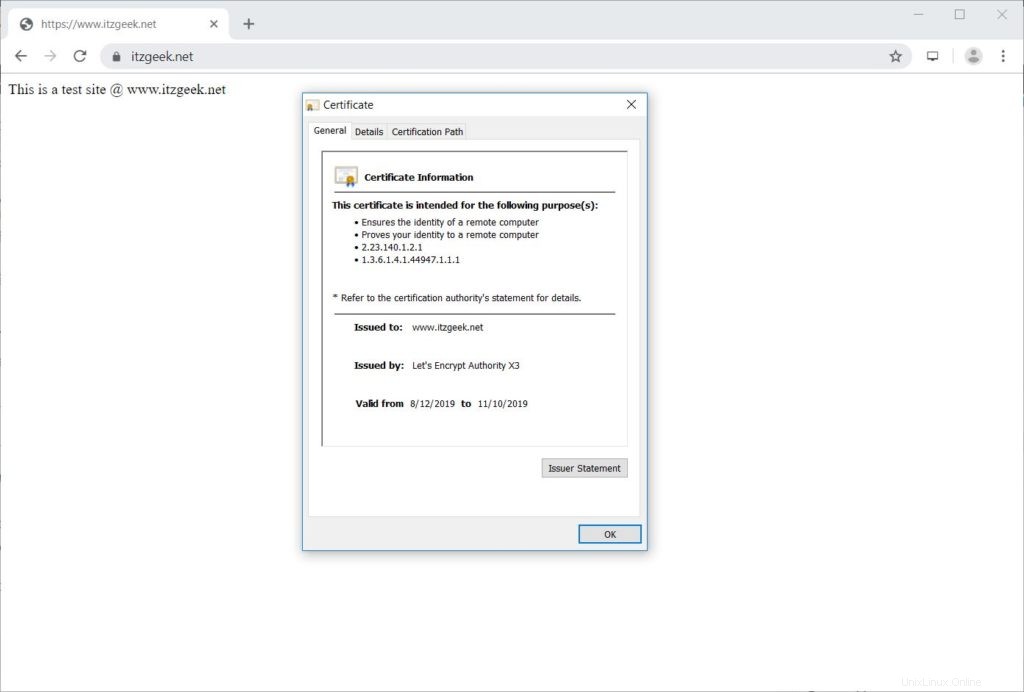
Probar el certificado SSL de Let's Encrypt
Pruebe su certificado SSL en busca de problemas y sus clasificaciones de seguridad yendo a la siguiente URL.
https://www.ssllabs.com/ssltest/analyze.html?d=www.itzgeek.net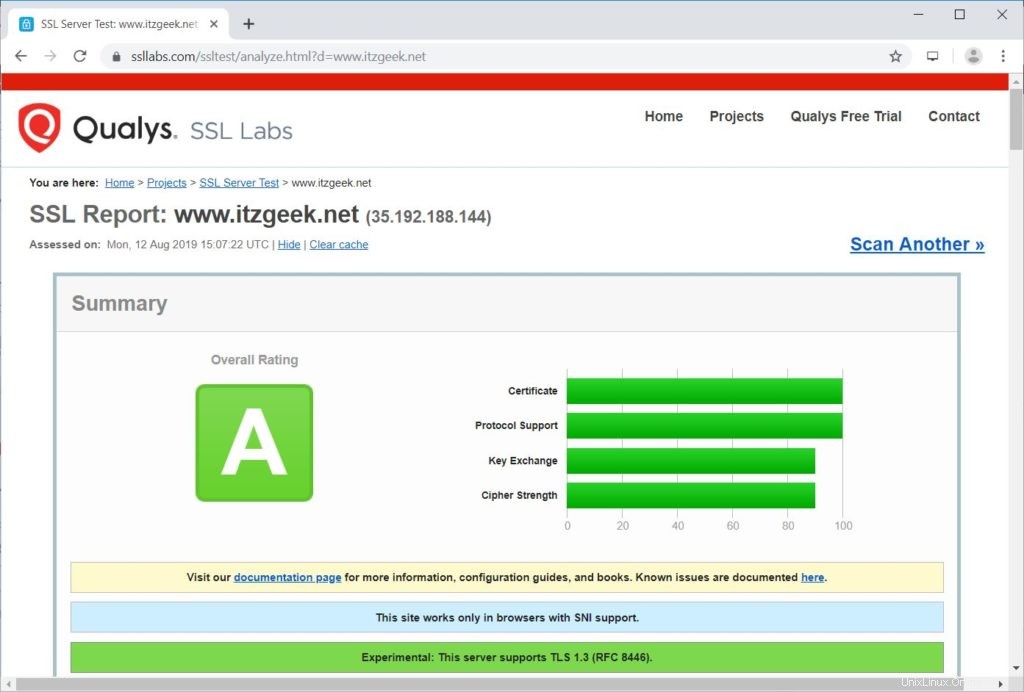
Renovar el certificado de Let's Encrypt
El certificado de Let's Encrypt es válido durante 90 días a partir de la fecha de emisión y debe renovarse antes de que caduque.
En CentOS 7/RHEL 7, de forma predeterminada, el cliente certbot crea una entrada en el programador cron para renovar los certificados de Let's Encrypt automáticamente.
Desafortunadamente, para CentOS 8/RHEL 8, necesitamos configurar el programador cron manualmente.
echo "0 0,12 * * * root python -c 'import random; import time; time.sleep(random.random() * 3600)' && /usr/local/bin/certbot-auto renew" | sudo tee -a /etc/crontab > /dev/null
También puede simular el proceso de renovación del certificado con el siguiente comando para asegurarse de que la renovación se realice sin problemas.
### CentOS 8 / RHEL 8 ### /usr/local/bin/certbot-auto renew --dry-run ### CentOS 7 / RHEL 7 ### certbot renew --dry-runPara renovar el certificado de Let's Encrypt, ejecute el comando anterior sin
--dry-run opción. Salida:
Saving debug log to /var/log/letsencrypt/letsencrypt.log - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Processing /etc/letsencrypt/renewal/www.itzgeek.net.conf - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Cert not due for renewal, but simulating renewal for dry run Plugins selected: Authenticator apache, Installer apache Renewing an existing certificate Performing the following challenges: http-01 challenge for www.itzgeek.net Waiting for verification... Cleaning up challenges - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - new certificate deployed with reload of apache server; fullchain is /etc/letsencrypt/live/www.itzgeek.net/fullchain.pem - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - ** DRY RUN: simulating 'certbot renew' close to cert expiry ** (The test certificates below have not been saved.) Congratulations, all renewals succeeded. The following certs have been renewed: /etc/letsencrypt/live/www.itzgeek.net/fullchain.pem (success) ** DRY RUN: simulating 'certbot renew' close to cert expiry ** (The test certificates above have not been saved.) - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - IMPORTANT NOTES: - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal.
Si el resultado no informa ningún problema, la renovación del certificado funcionará como se esperaba.
Conclusión
Eso es todo. Espero que haya aprendido a configurar el certificado Let's Encrypt SSL con Apache en CentOS 8/RHEL 8 y CentOS 7/RHEL 7. Comparta sus comentarios en la sección de comentarios.